Configuring SSO
This version of the Anyscale docs is deprecated. Go to the latest version for up to date information.
Configuring Single Sign On (SSO) for an Anyscale organization requires two distinct steps:
- Configuring the Identity Provider (IdP). This is Okta, Ping Identity or a similar service.
- Configuring the Service Provider (SP). This is Anyscale.
IdP Configuration
The exact steps to configure an IdP vary between provider. Ensure that all steps are completed before moving on to configure Anyscale. If your organization uses an IdP other than the following, please contact Anyscale support as additional allow-listing may be necessary.
After you complete IdP configuration, continue with SP Configuration.
- Okta
- Google Workspaces
- Ping Identity
- Azure AD
-
Log in to your organization's admin Okta account, this is the
admin-<organization>.okta.comdomain. -
Navigate to the “Applications tab.
-
Create a new app integration by clicking the Create App Integration button and select the
SAML 2.0option.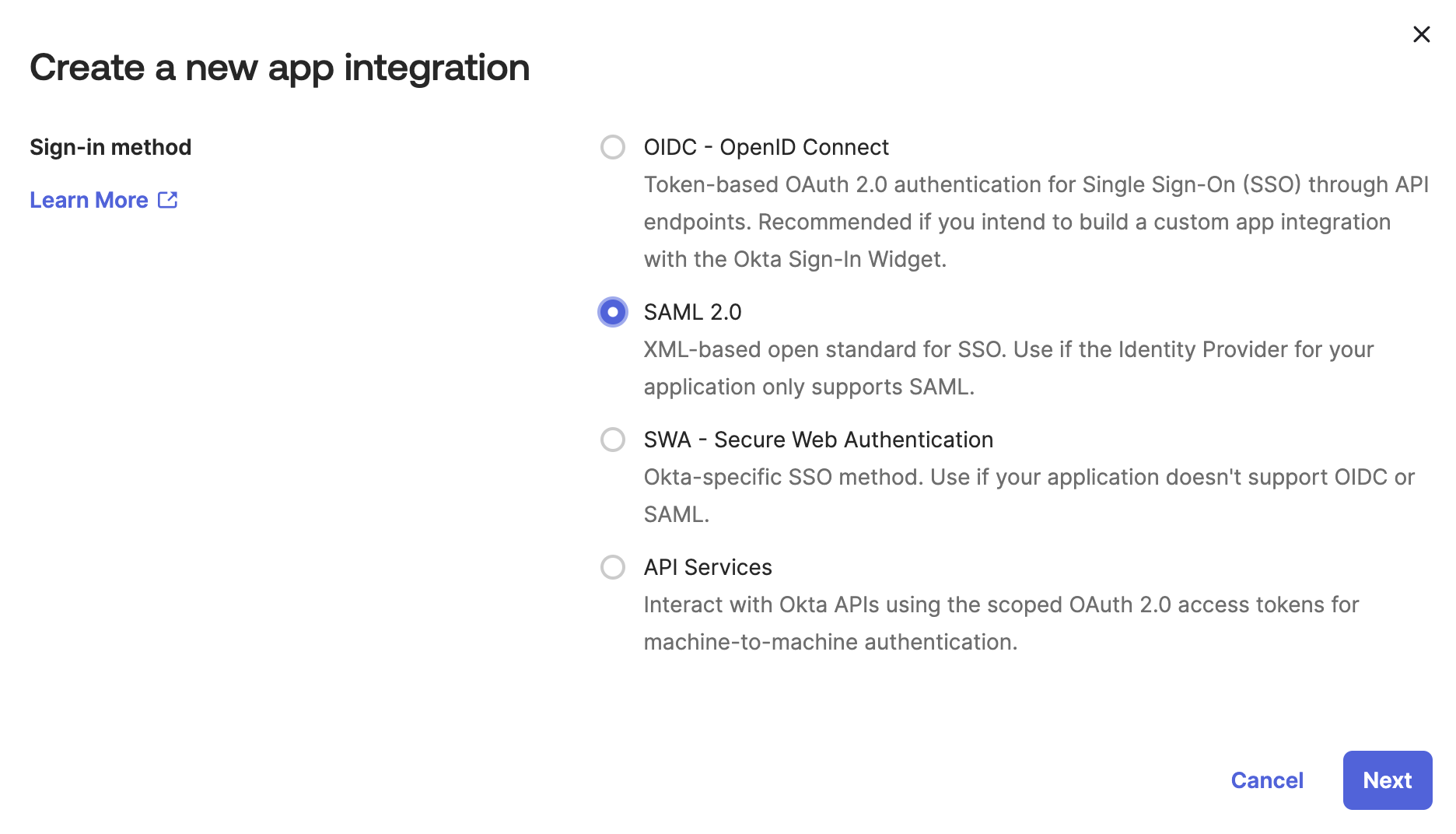
-
Add an appropriate App Name and (optionally) App logo.
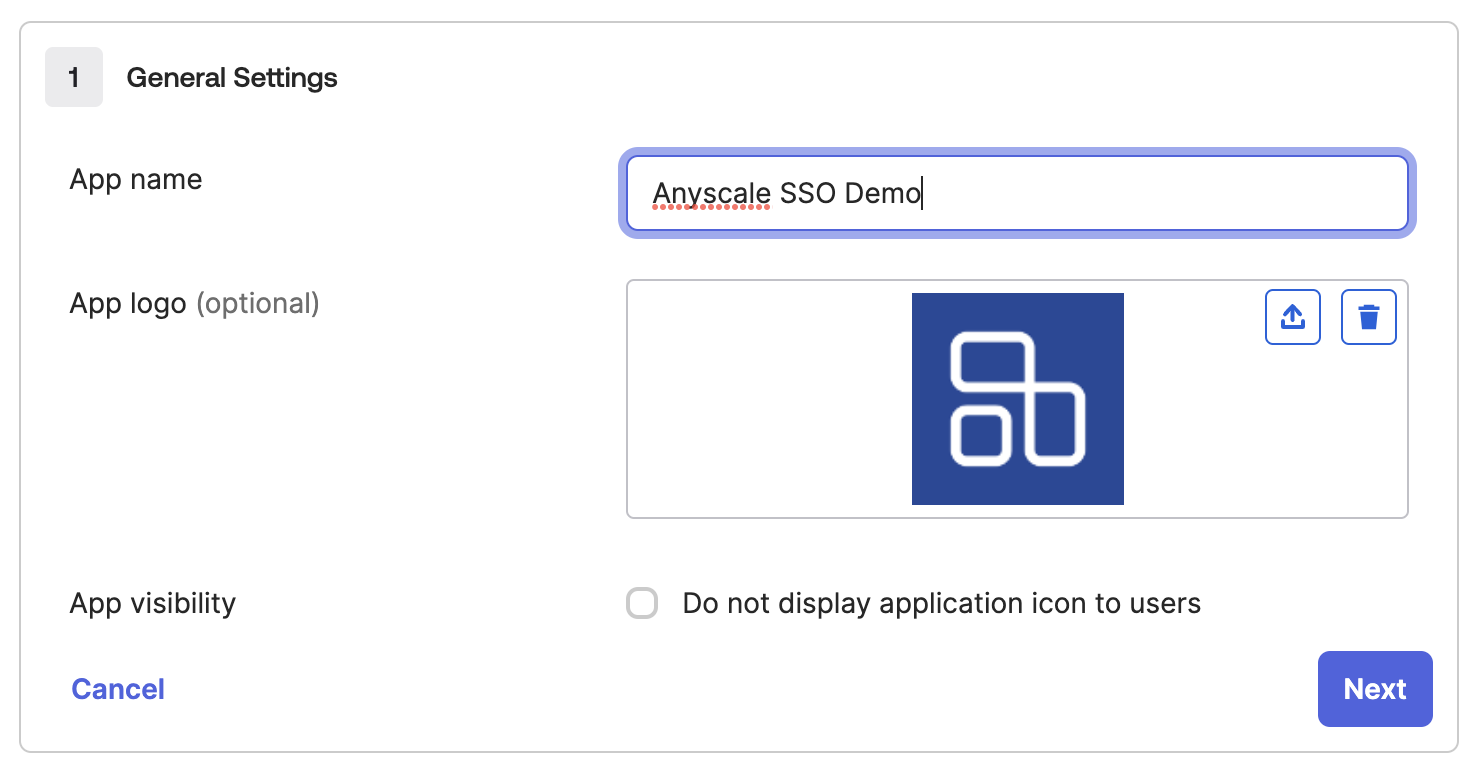
-
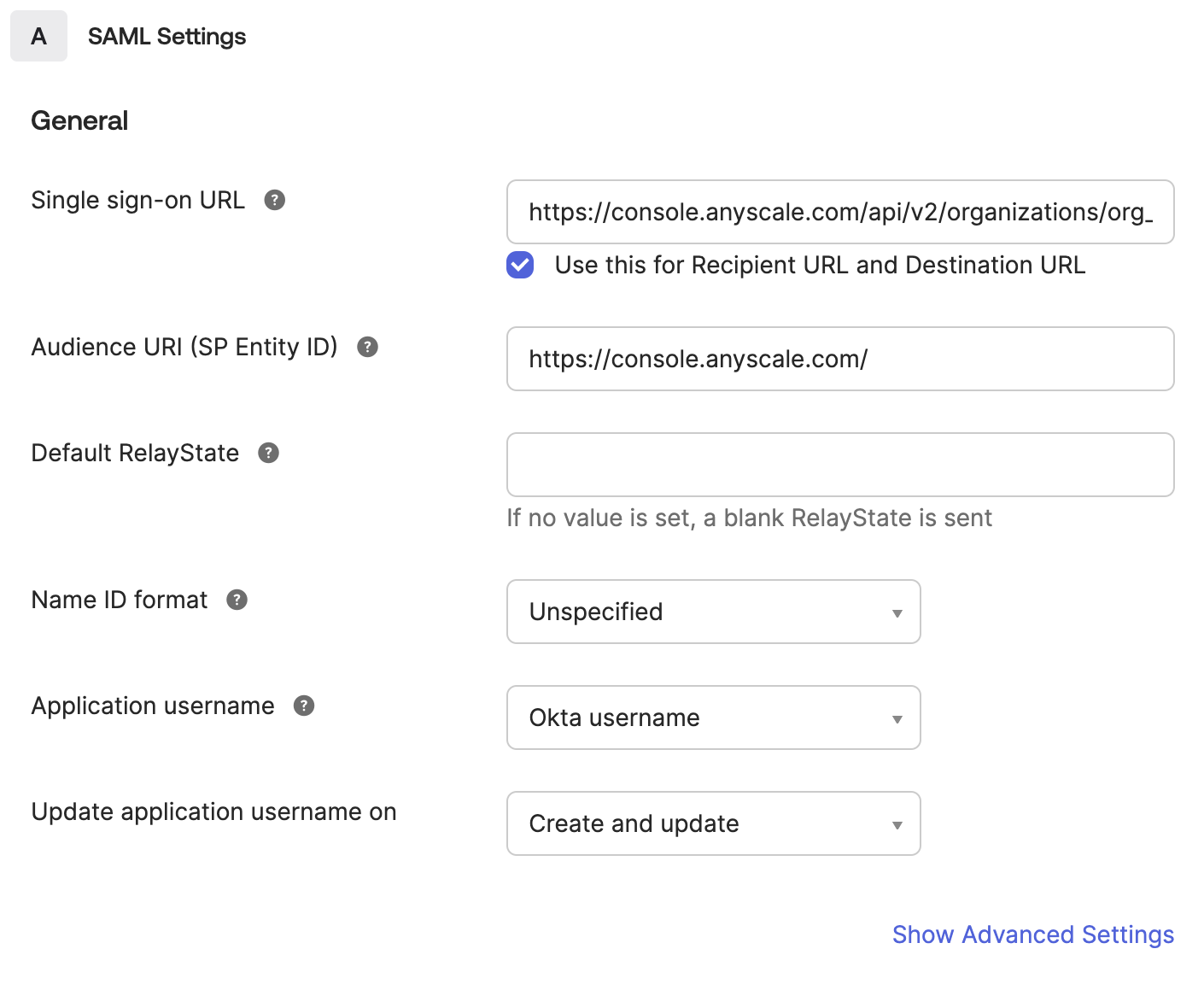
Continue to the Configure SAML page and fill out the following two fields:
- Single sign-on URL: Find your
organization_idhere.
https://console.anyscale.com/api/v2/organizations/<organization_id>/saml_acs
- Audience URI (SP Entity ID): Note that the trailing
/is required.
https://console.anyscale.com/
-
Scroll down and fill out the Attribute Statements. Anyscale requires that
email,nameandusernameattributes are provided. The source of each value is not important to Anyscale.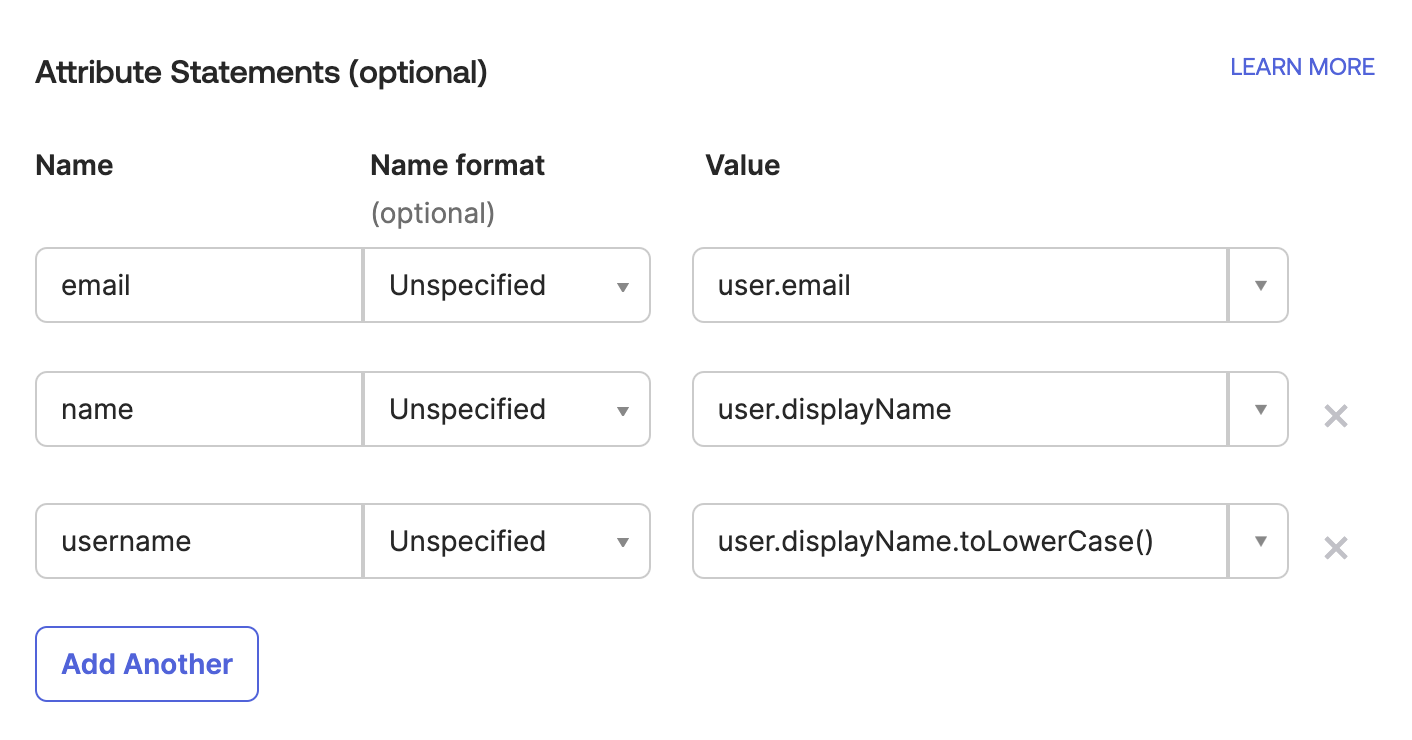
-
Finish application configuration by clicking next and completing the Feedback page.
-
Ensure that your integration is active and assign appropriate users to the application.
These directions are based on Google's official documentation, but are tailored to Anyscale's specific requirements.
-
Log in to your Google Workspace account with administrative privileges.
-
Navigate to the Google Admin Console.
-
Expand the Apps menu in the left side bar and select Web and mobile apps.
- Select Add App menu and click the Add custom SAML app option.
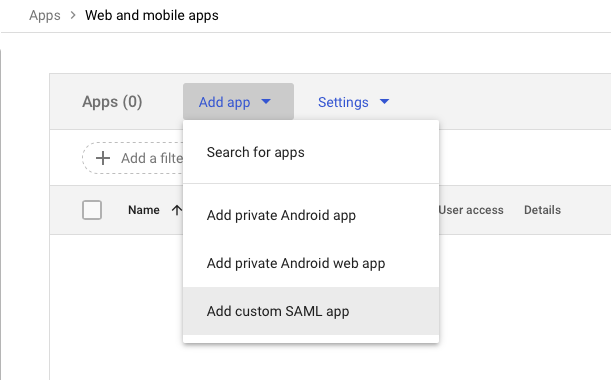
- Add an appropriate App Name and (optionally) App logo.
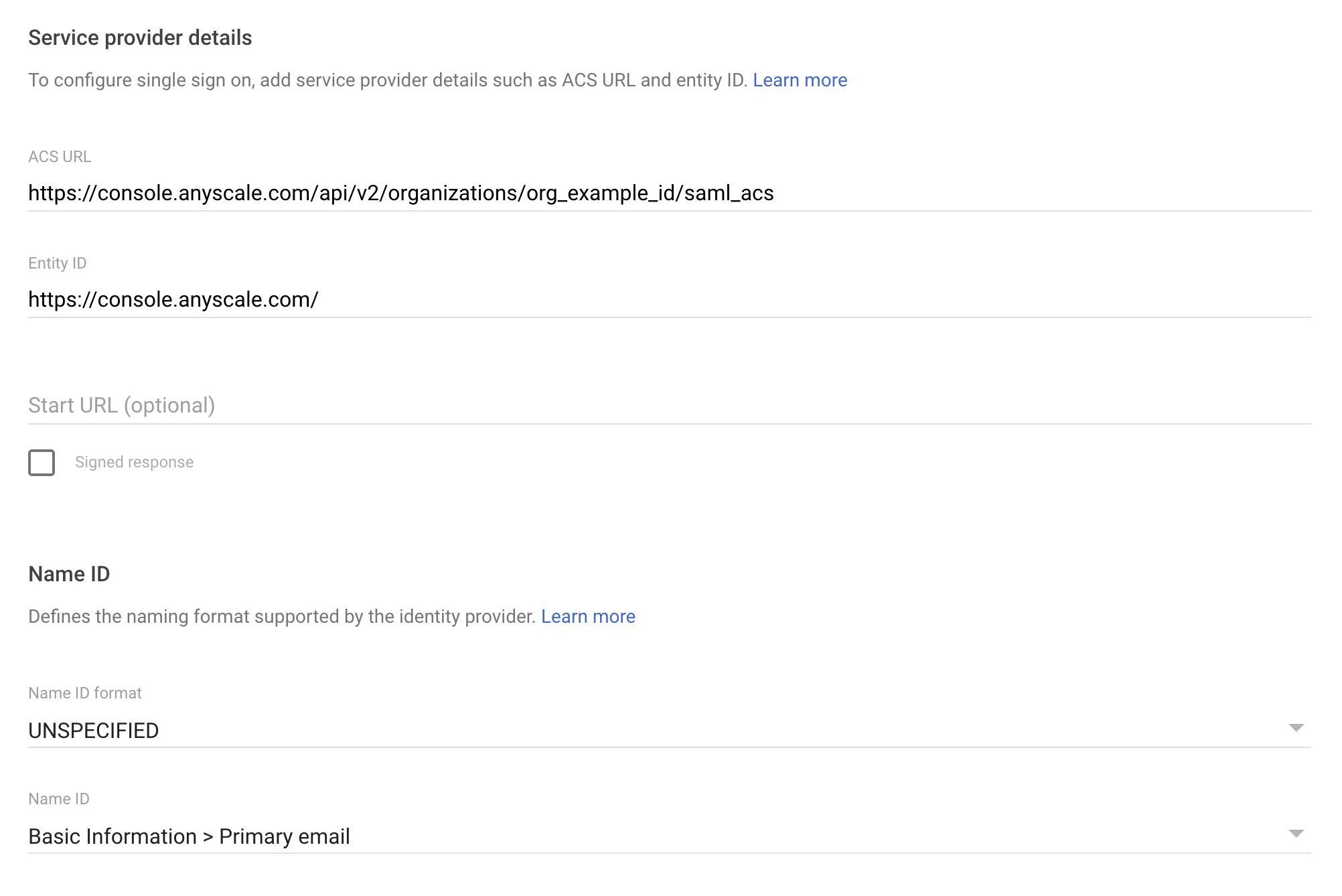
- Continue pass the Google Identity Provider Details page and fill out the following two fields on the Service Provider Details page:
- ACS URL: Find your
organization_idhere.
https://console.anyscale.com/api/v2/organizations/<organization_id>/saml_acs
- Entity ID: Note that the trailing
/is required.
https://console.anyscale.com/
- Continue to the Attribute mapping page and add the three attributes that Anyscale requires:
email,nameandusername. The source of these values is not important to Anyscale.
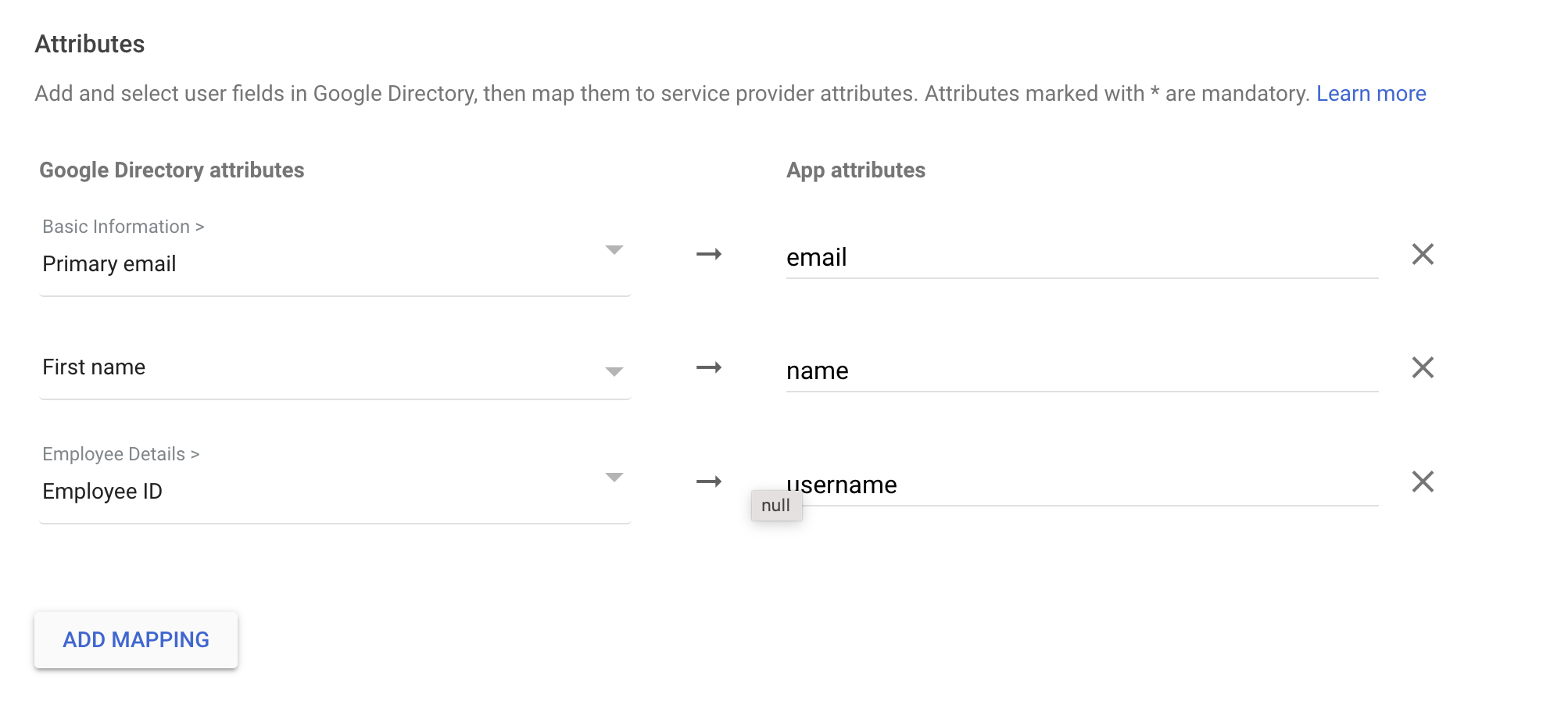
- Click Finish.
- Log in to your Pingone account as an admin.
- Navigate to the Connections tab and select Applications.
-
Click the + button next to the Applications heading.
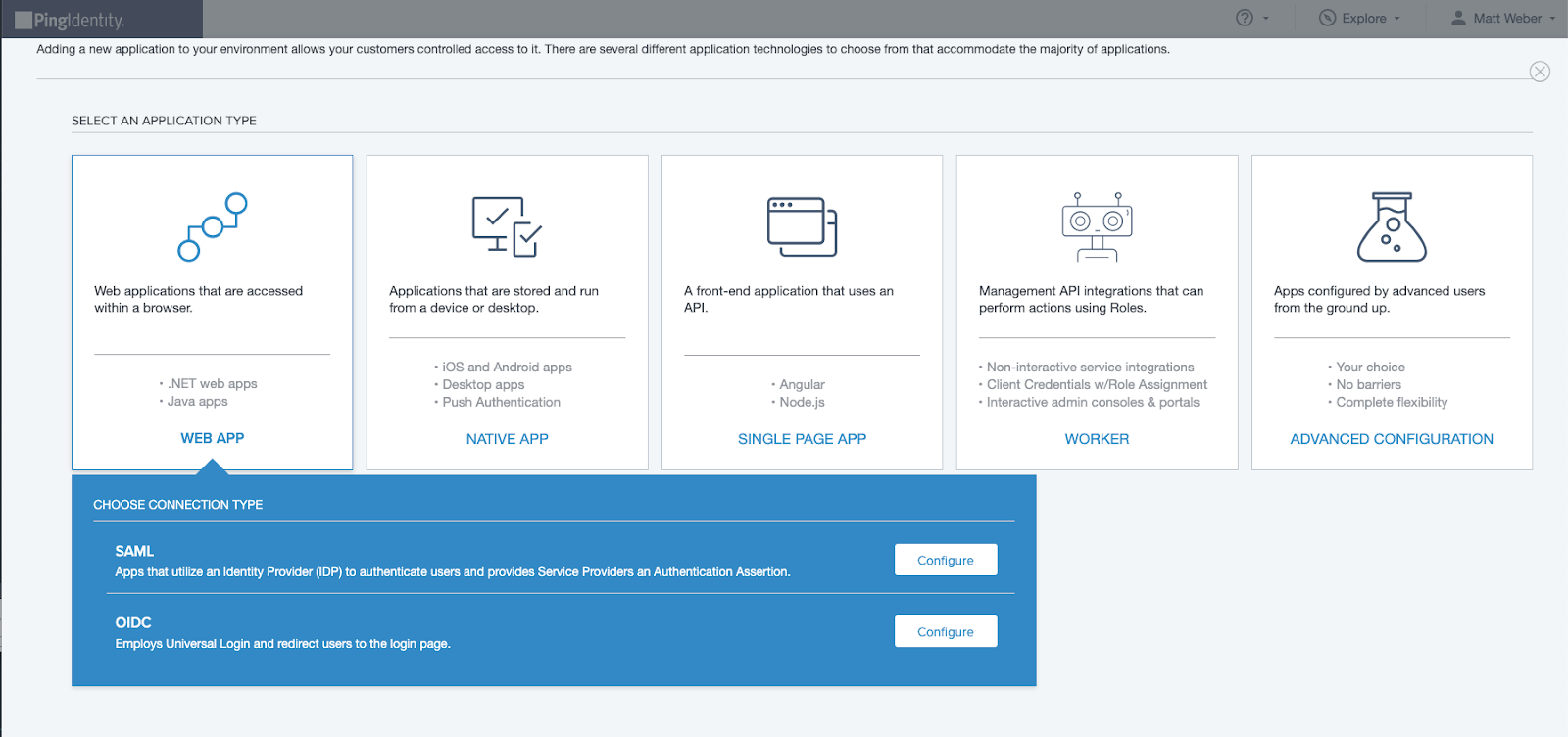
-
Select WEB APP as the desired application type and SAML as the connection type.
-
Add an appropriate Application Name and (optionally) an Icon.
-
Manually enter the ACS URL using the following format.
https://console.anyscale.com/api/v2/organizations/<organization_id>/saml_acs
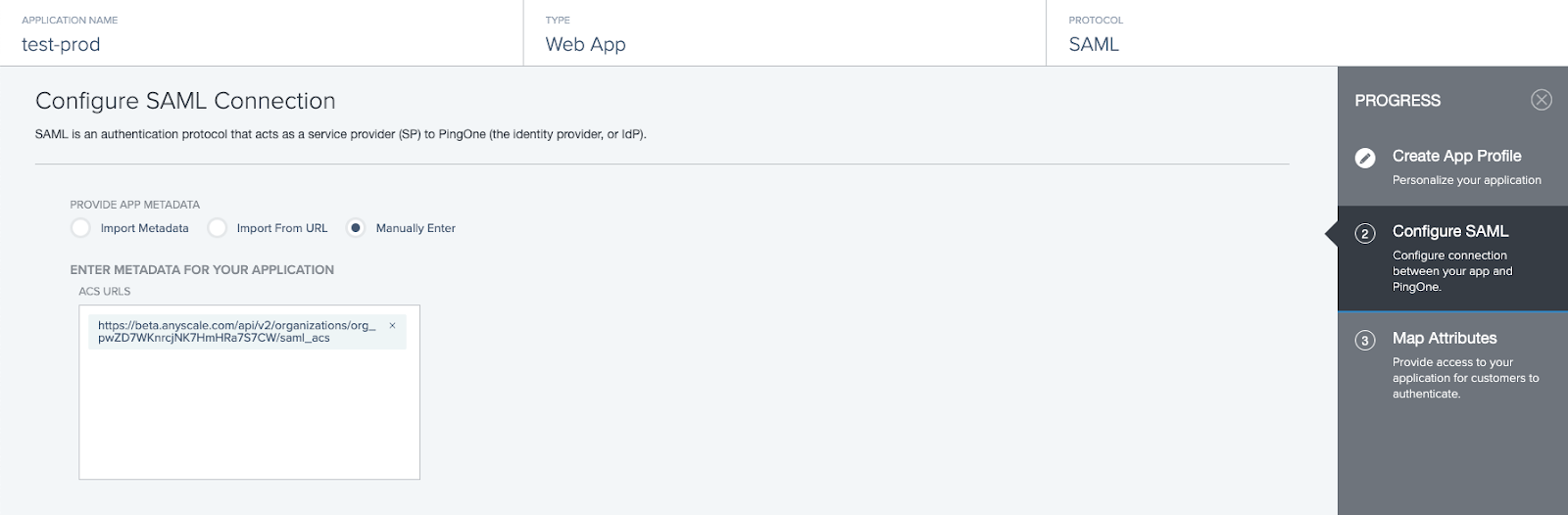
- Add the ENTITY ID as follows. Note that the trailing
/is required.
https://console.anyscale.com/

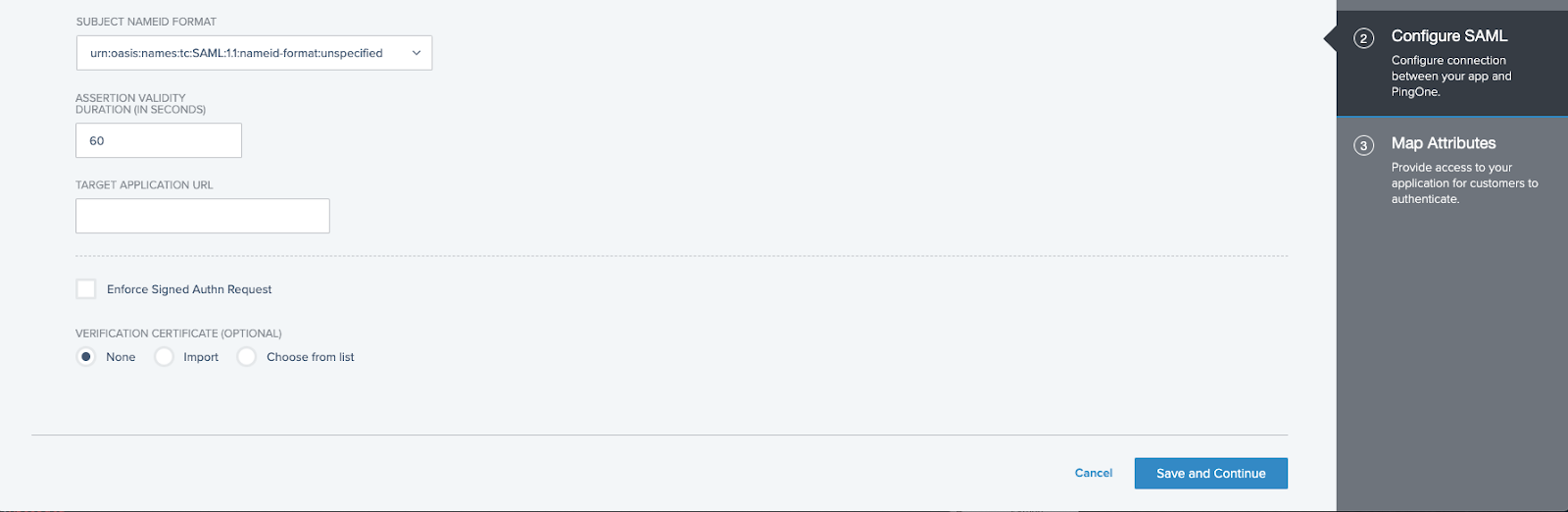
- Specify a value for ASSERTION VALIDITY DURATION (60 seconds is a reasonable default) and click Save and Continue.
-
On the Map Attributes page, add the following three required application attributes
email,nameandusername. The corresponding source PingOne User Attribute is not important to Anyscale.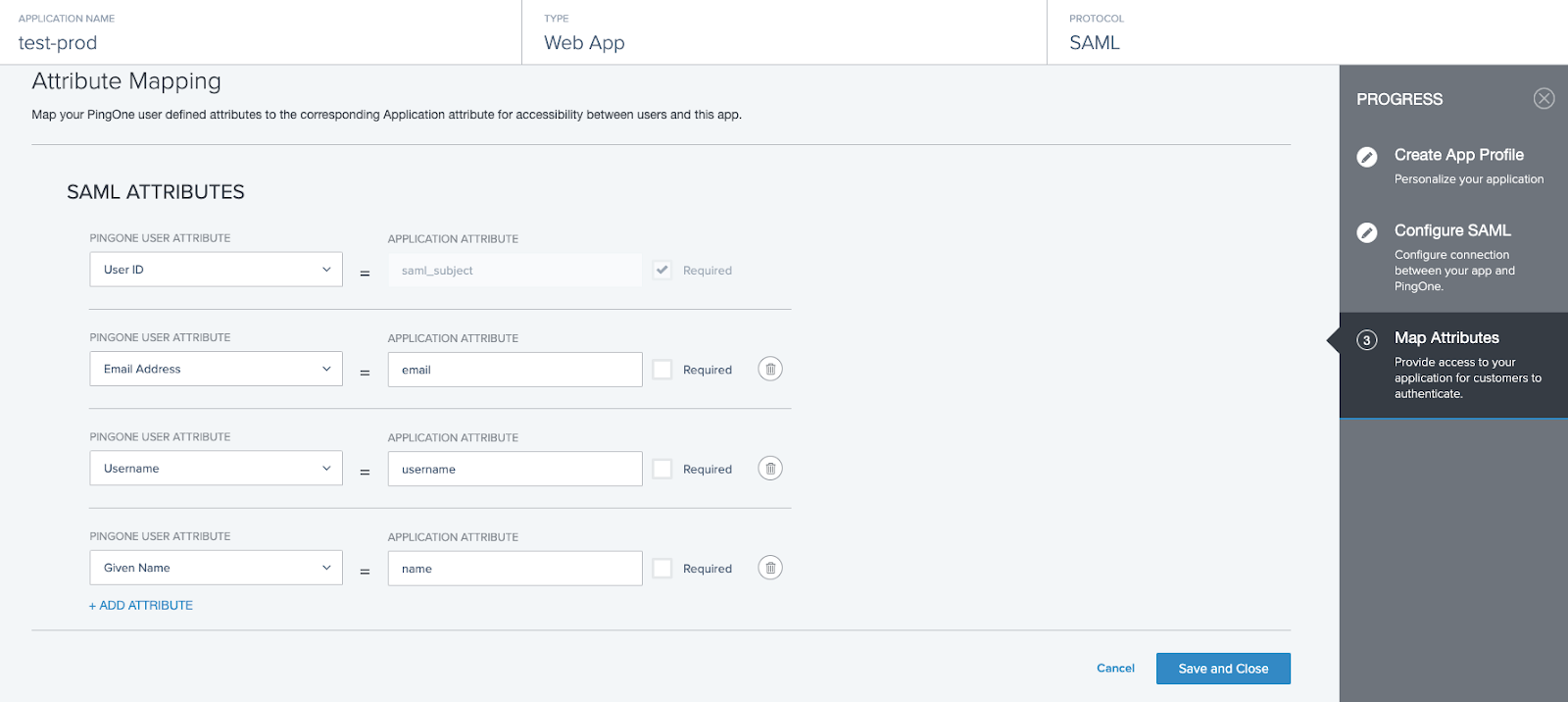
-
Click Save and Continue.
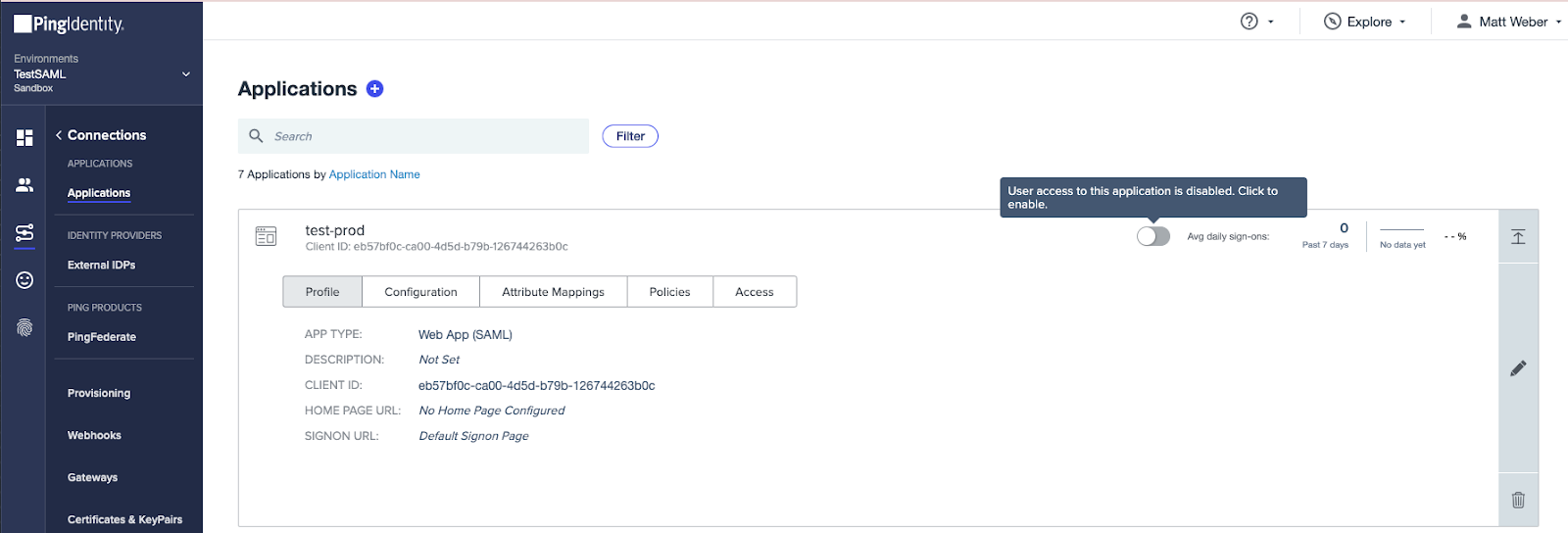
-
Ensure that your application is enabled.
-
Log in to your account as an administrator.
-
Select Enterprise applications from under the Manage menu on the left panel.
-
Click the + New Application at the top of the page.
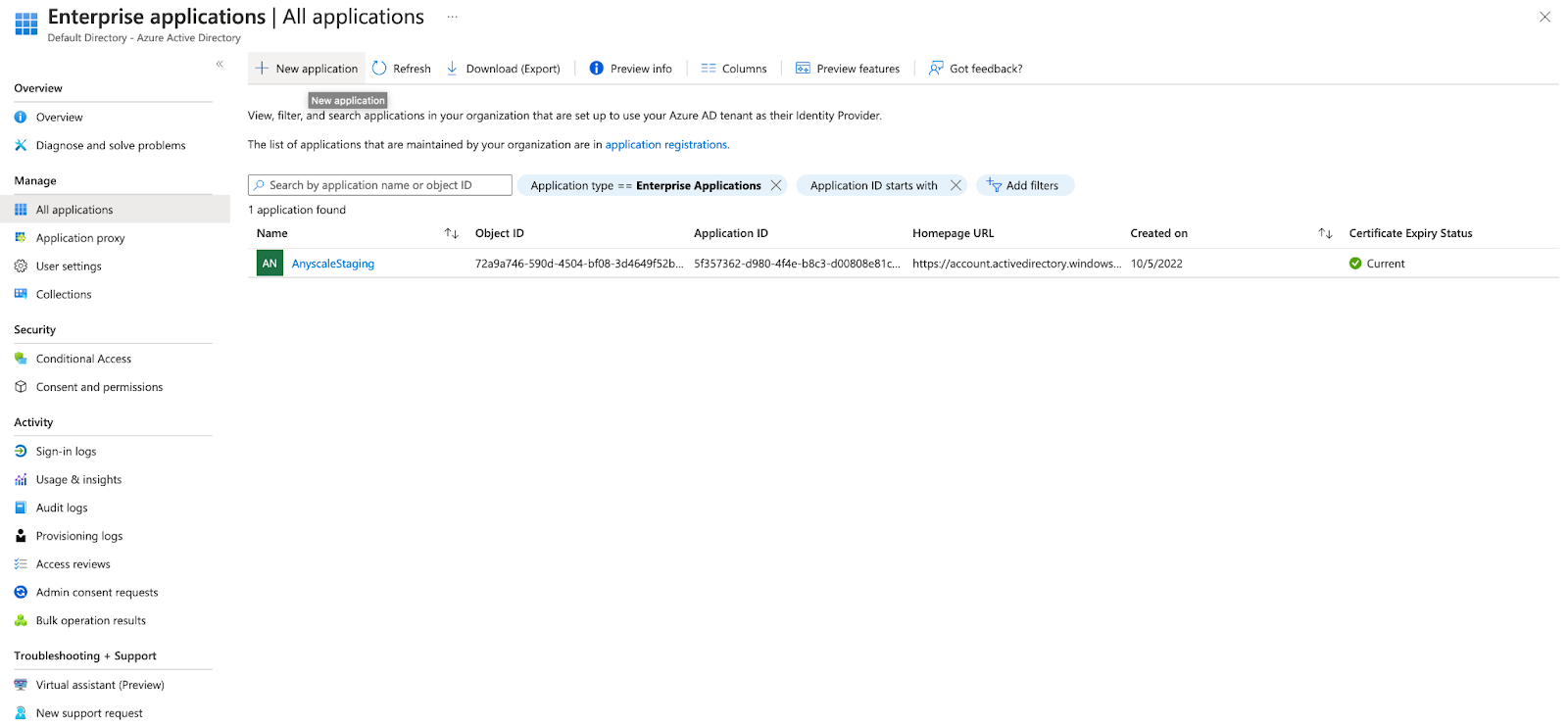
- Select + Create your own application at the top left.

- In the pop-up window, enter an appropriate Name and select Integrate any other application you don't find in the gallery (Non-gallery) and click Create.
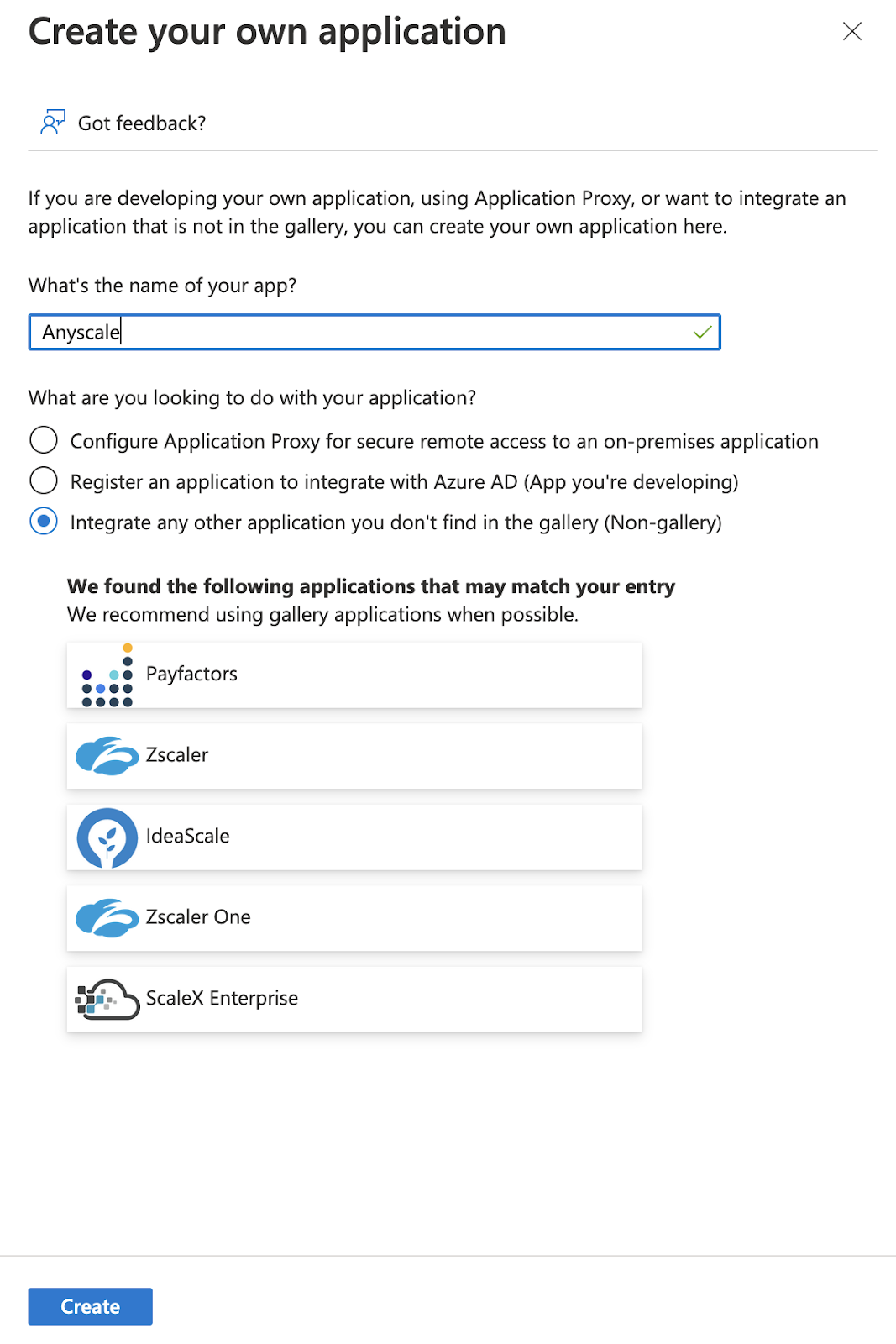
- You should now see an Overview page for your newly created application.
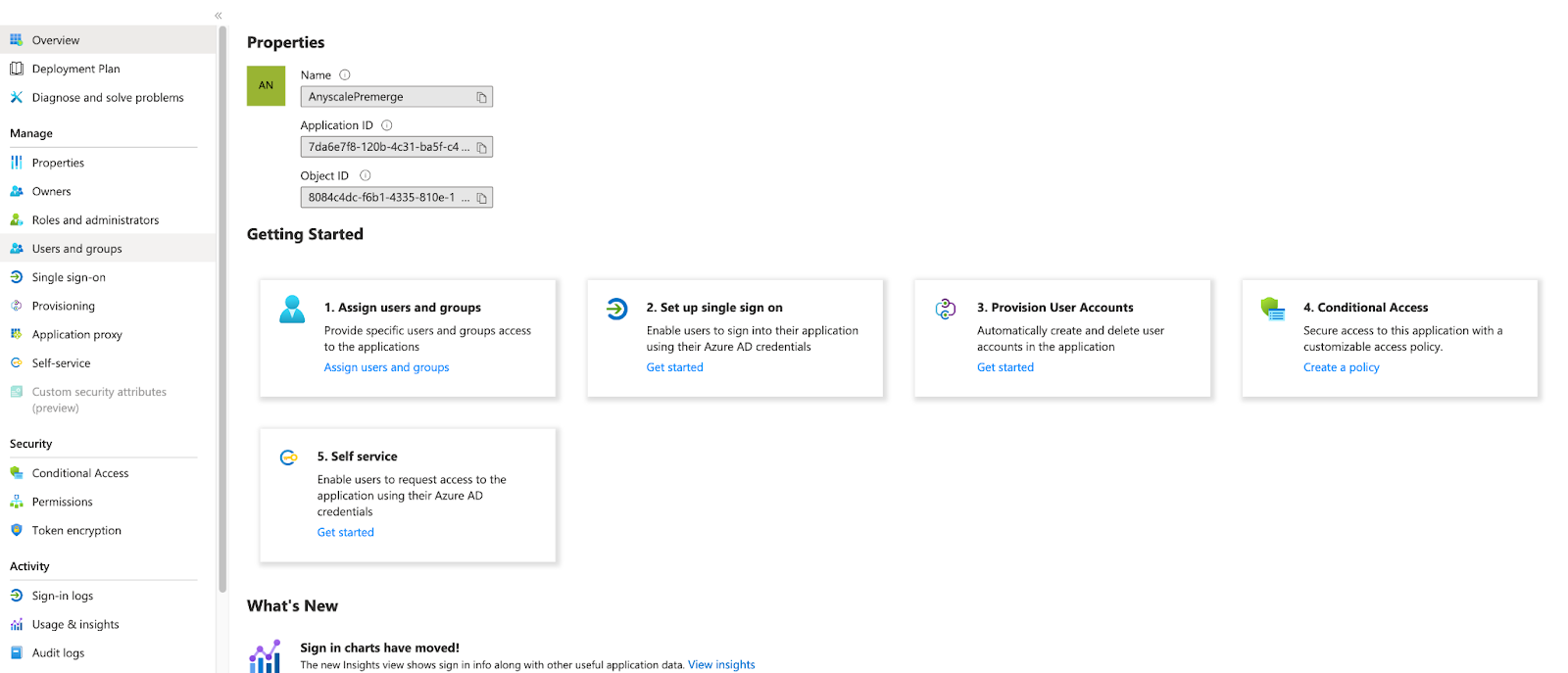
- Select the Set up single sign on card from the Getting Started menu. Alternatively, select Single sign-on from the left side menu. Click SAML as the sign-on method.
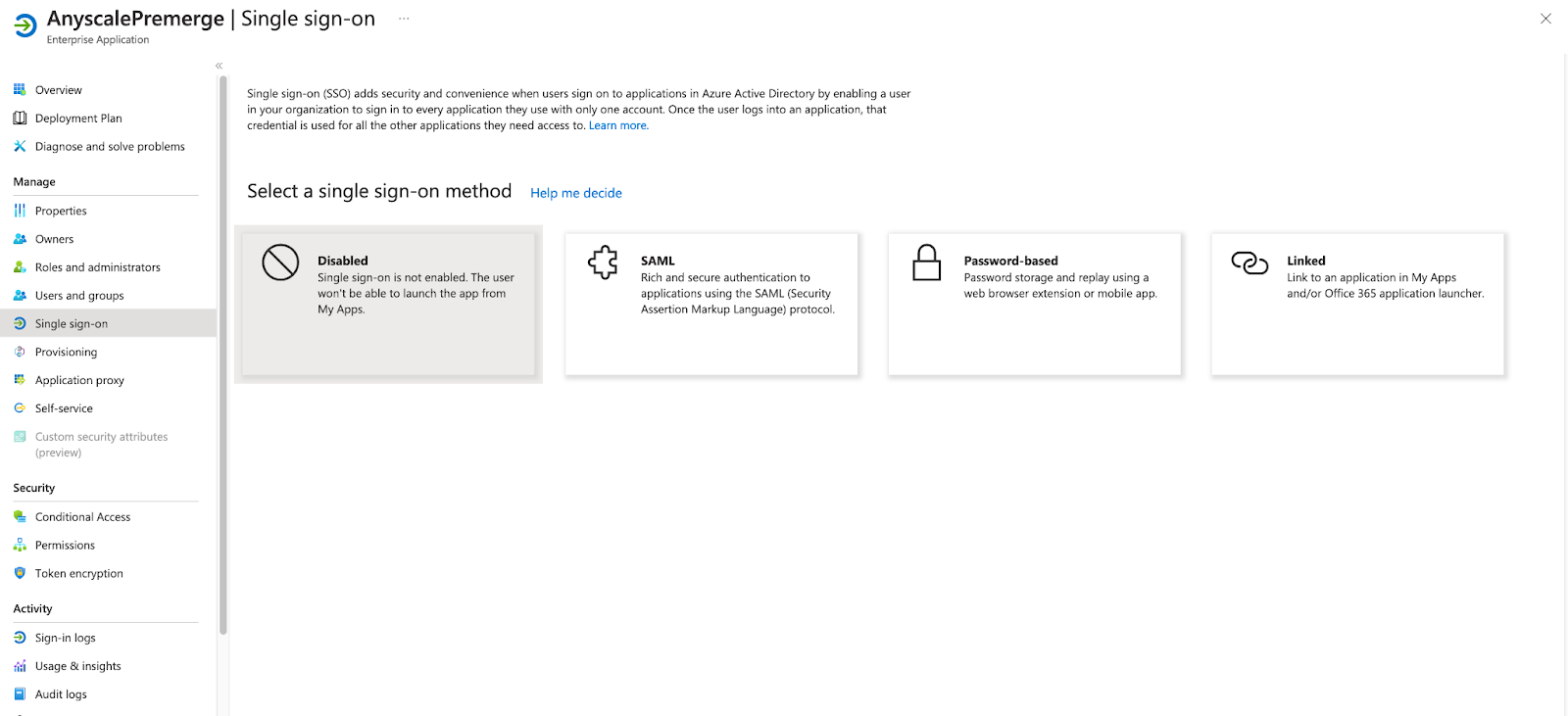
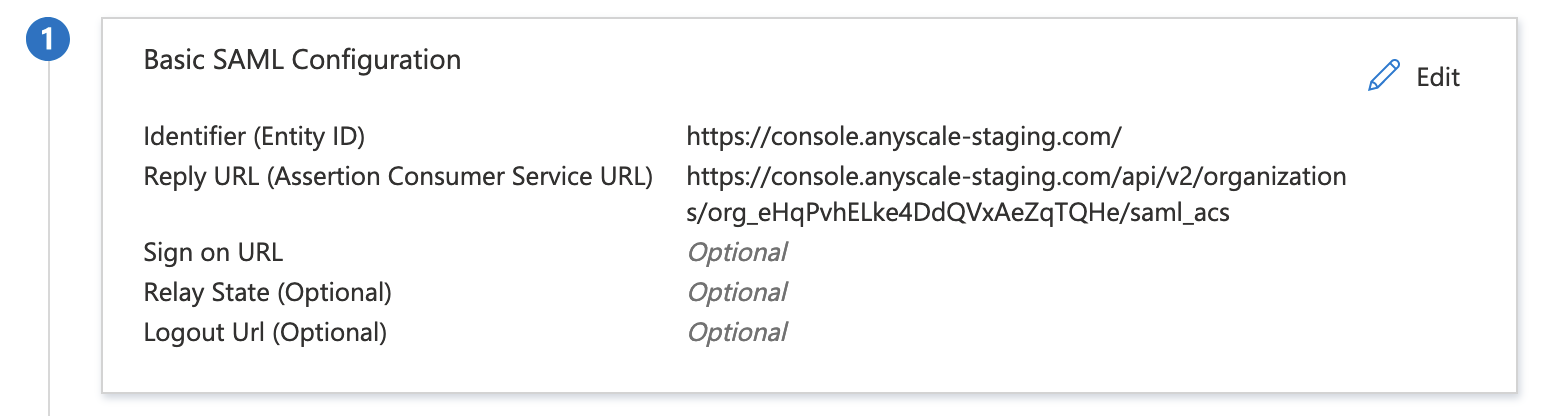
- Edit the Basic SAML Configuration card and fill out the Identifier and Reply URL fields as follows:
- Identifier (Entity ID): Note that the trailing
/is required.
https://console.anyscale.com/
- Reply URL (Assertion Consumer Service URL): Find your
organization_idhere.
https://console.anyscale.com/api/v2/organizations/<organization_id>/saml_acs
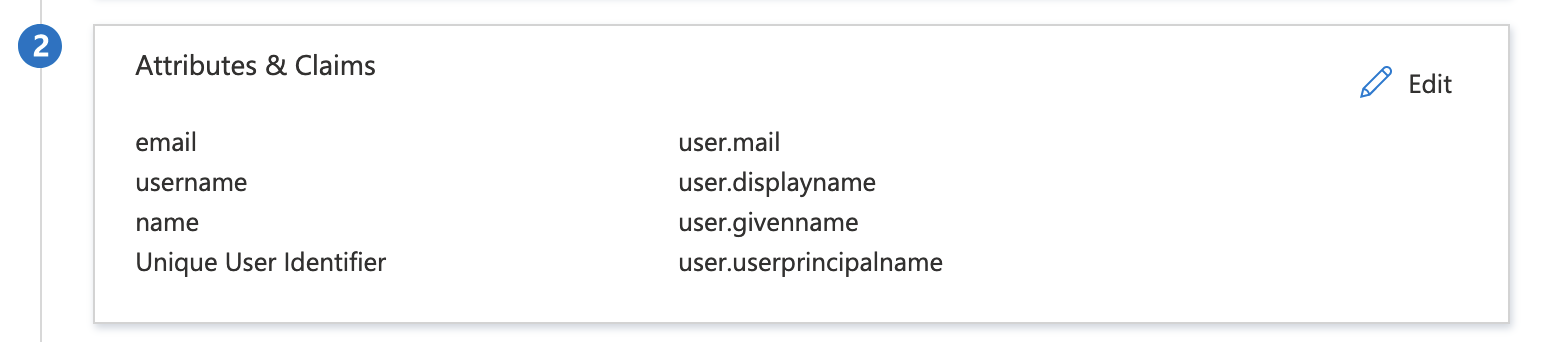
- Edit the Attributes & Claims card to include the following three required attributes:
email,nameandusername. The source of each of these values is not important to Anyscale.
Azure AD requires every application to have a unique Identifier (Entity ID). This is problematic if you need to use Azure AD to connect to multiple Anyscale organizations because all would have the same Entity ID of https://console.anyscale.com/.
To work around this, first specify the Identifier (Entity ID) to a unique value for each Anyscale organization in the Basic SAML configuration. Then, go to the Advanced settings on the Attributes & Claims page and override the audience to be https://console.anyscale.com/. This will ensure that the correct entity id is sent during the SAML flow.
SP Configuration (Anyscale)
Only Anyscale Organization administrators can configure SSO. Ensure that you are signed in with the appropriate account before continuing.
- Acquire the
idp_metadata_url(a URL used to retrieve your IdPs metadata) orstatic_idp_config(static metadata for your IdP, fields shown below) from your IdP. The metadata URL is preferred as it is easier to include and will not require reconfiguration in the future. If you are not using one of the 4 providers used in this guide, collect the required information and skip to step 3.
{
"idp_entity_id": "string",
"idp_sso_url": "string",
"idp_sso_binding": "string",
"idp_x509cert": "string"
}
- Okta
- Google Workspaces
- Ping Identity
- Azure AD
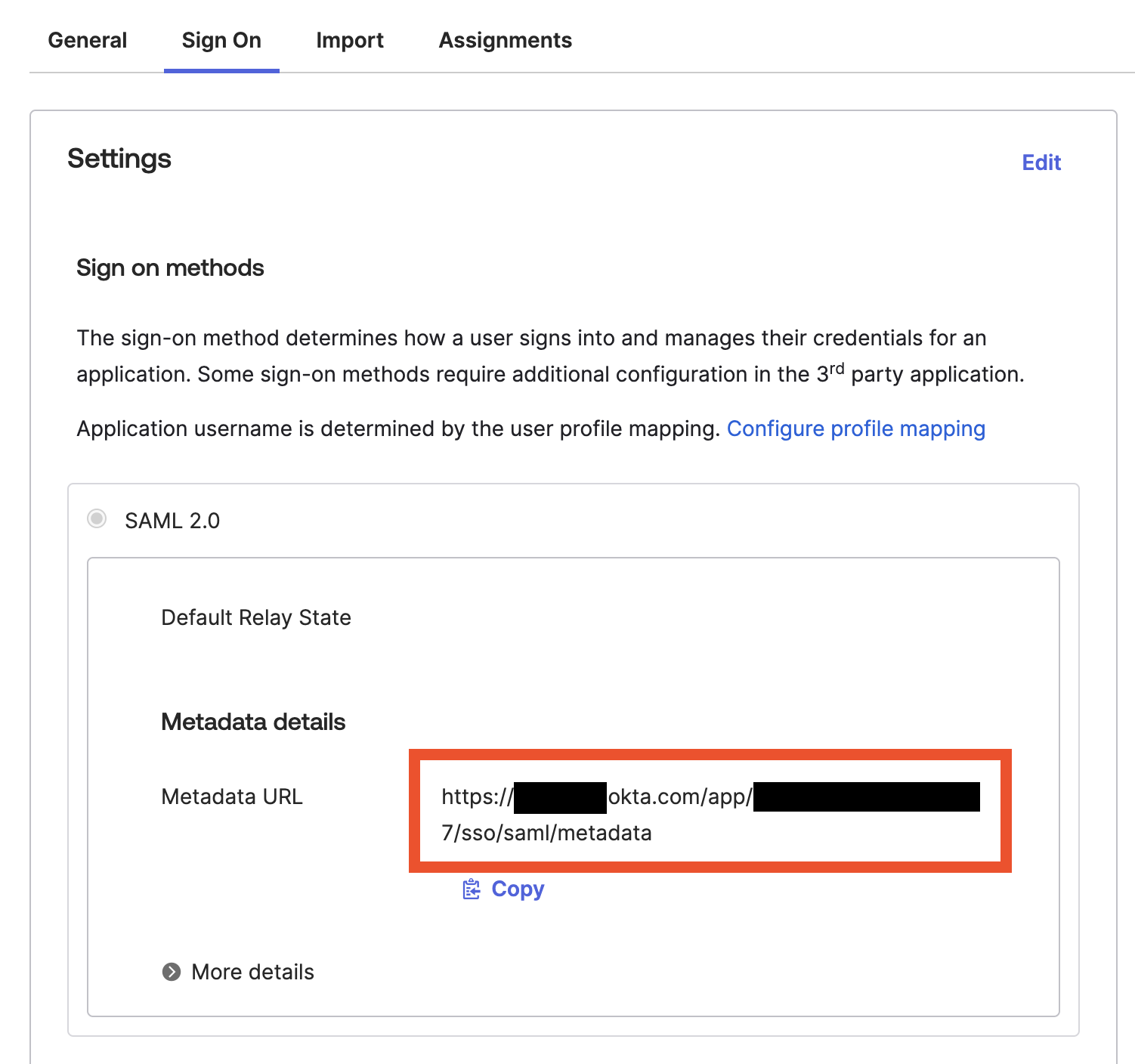
- Okta supports an
idp_metadatal_urlfor sign-on. Navigate to your applications Sign On tab and copy the Metadata URL field for use in the next step.
- Google does not have a metadata URL endpoint, so specifying the
static_idp_configis required. Navigate to your Custom SAML app and click Download Metadata.
{
"idp_entity_id": "", // SSO URL
"idp_sso_url": "", // Entity ID
"idp_sso_binding": "urn:oasis:names:tc:SAML:2.0:bindings:HTTP-Redirect",
"idp_x509cert": "" // Certificate
}
- Navigate to your Application, head to the Configuration tab and click Download metadata.
- Navigate to your Application and go to the Single sign-on tab. Locate the SAML Certificates card and copy the App Federation Metadata URL for use in the next step.
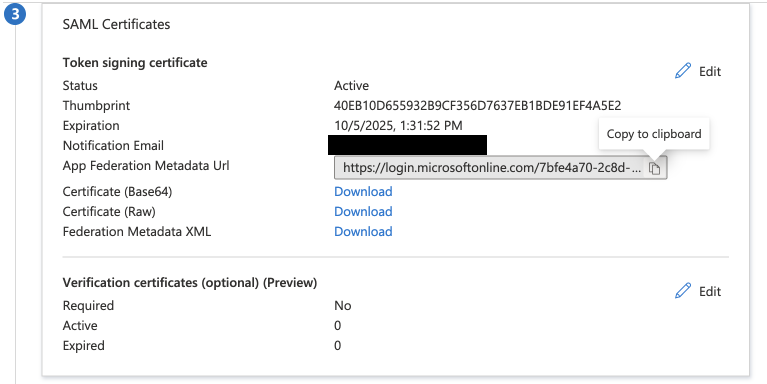
- Navigate to the API docs page https://console.anyscale.com/ext/v0/docs.
- Create (or update) your organization's SSO configuration with the
/sso_configs/endpoint (titled Upsert Sso Config). Use only theidp_metadata_urlfield or thestatic_idp_configfield depending on what your IdP supports.
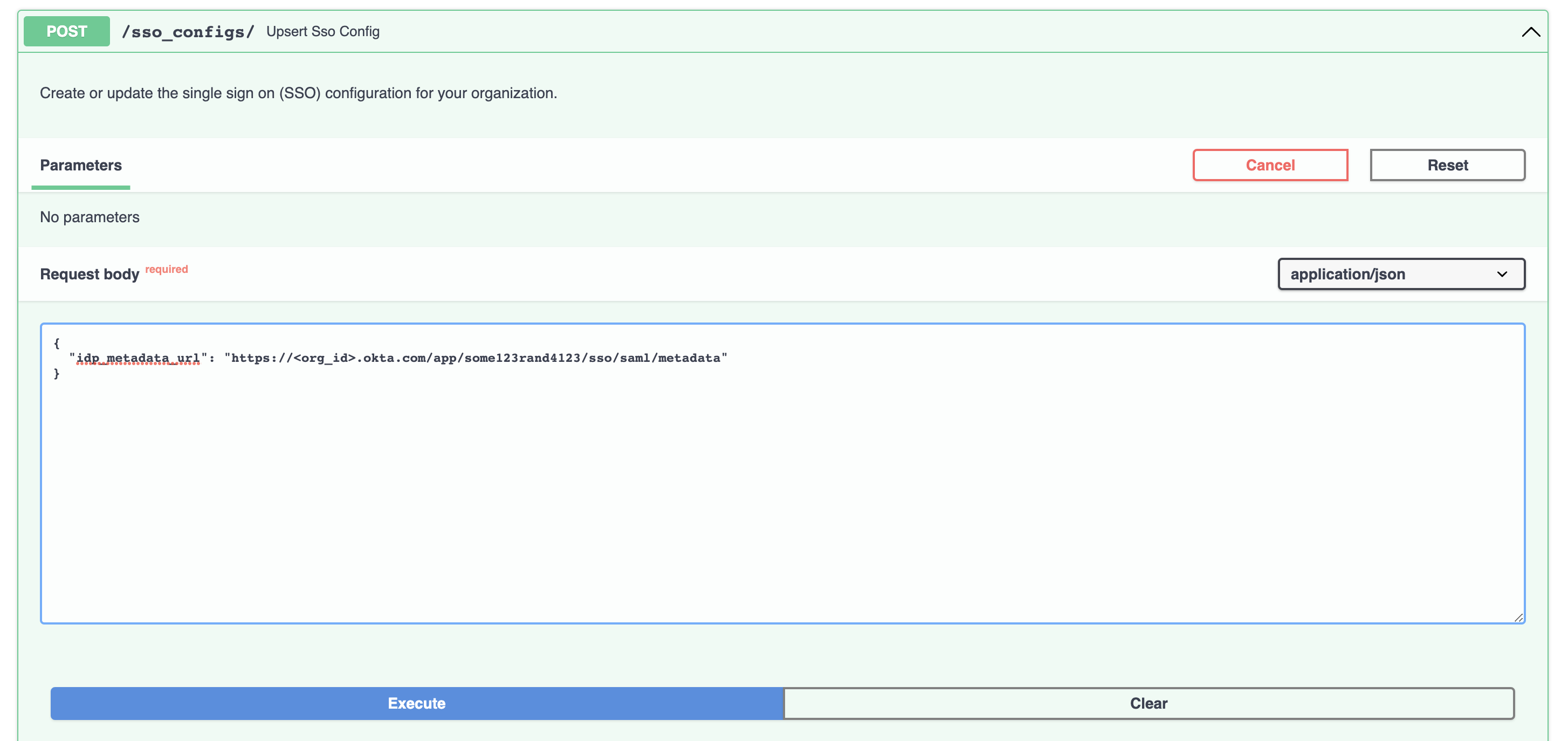
-
Click
Executeand ensure that the server response is200. -
Enable SSO for your Anyscale organization with the
/organizations/{organization_id}endpoint (titled Partial Organization Update). Specify your organization's ID in thepathfield and select thesso_modeto enforce. The three possible values ofsso_modeare listed below. It is recommended to start withoptionaland move torequiredonce you have verified that SSO is working as expected.
off: SSO login is not enabled for your organization.optional: SSO login is optional for your organization. Users normally log in with SSO, but can also log in with a password.required: SSO login is the only way for users to log in to your organization.
When SSO is made required, the current SSO configuration will be the only way for most users to log into the organization. Organization Admins can always log in with Anyscale with a password. If you are not 100% confident that the SSO configuration is correct, or if you need to use a username/password for service accounts, use the string optional mode.
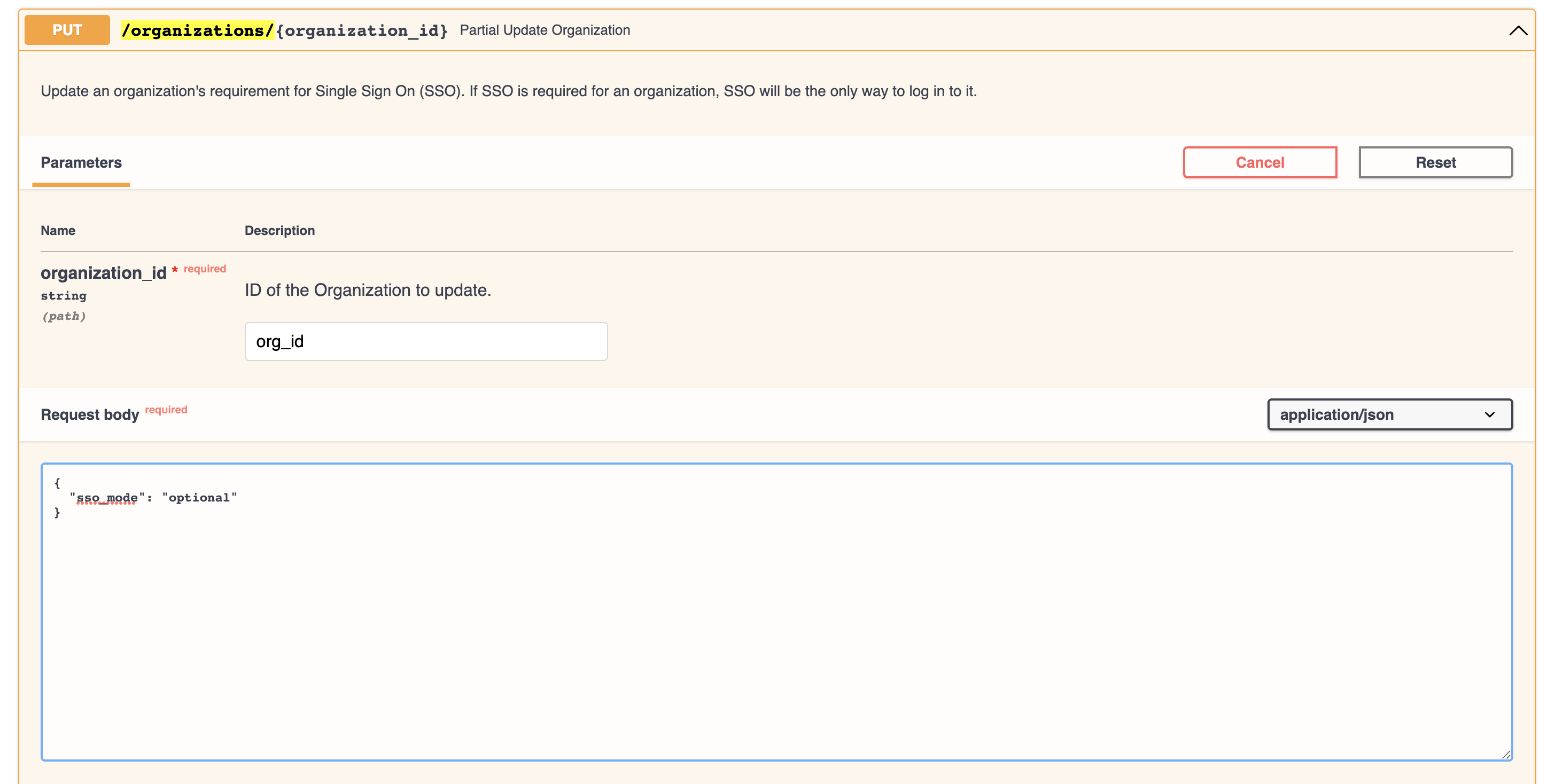
-
Click
Executeand ensure that the server response is200. -
Log in to Anyscale (preferably in a separate browser or in a private browsing window) to verify that the SSO log in flow with your IdP works as expected.
Fallback Access
Anyscale Organization admins always have the ability to log in to Anyscale with a username and password. This is a fallback mechanism in case SSO is unavailable or misconfigured. Admins can log in with the following CURL command:
curl -X POST https://console.anyscale.com/api/v2/users/login \
-H 'Content-Type: application/json' \
-d '{"email": "<email>", "password": "<password>", "organization_id": "<organization_id>"}'
Logging in with SSO
Once SSO is configured, there are two ways users can log in to Anyscale: IdP initiated and SP initiated.
IdP Initiated
The IdP initiated flow begins from your identity provider (for example, Okta or Azure AD). Log in to your IdPs website and select the link for Anyscale. If Anyscale is not visible, ensure that your user has been assigned to the application.
First-time Anyscale users must use the IdP initiated flow to log in to Anyscale in order to trigger just-in-time account creation.
SP Initiated
The SP initiated flow begins on the Anyscale homepage. Insert your work email and click Next. You should be automatically redirected to your IdP and then back to Anyscale.