Manage an Anyscale Cloud on GCP
The creator or assigned owner of an Anyscale Cloud can manage deployed cloud resources. The three main ways to modify an Anyscale Cloud are deleting, editing, and setting default resources.
Delete an Anyscale Cloud
To delete an Anyscale Cloud, follow these steps to ensure a safe and complete removal of all associated resources. This process involves terminating instances and clusters, running the deletion command, and understanding the post-deletion implications.
Step 1: Terminate all active instances and clusters
For all clusters with running, pending, and error statuses, follow the instructions in the UI to stop the workload. Verify in your GCP console that these cluster have no running instances.
Step 2: Delete the Cloud
Delete the Anyscale Cloud with the following command:
$ anyscale cloud delete --name ANYSCALE_CLOUD_NAME
Post-deletion implications
- After deleting an Anyscale Cloud, you can no longer create clusters, Workspaces, Jobs, or Services using this Cloud.
- Any clusters associated with the deleted Cloud are no longer accessible.
When you delete an Anyscale Cloud that you set up using anyscale cloud setup, all associated resources are also removed.
However, deleting a cloud created using anyscale cloud register doesn't automatically remove any GCP resources you created. To revoke Anyscale's access to these GCP resources, you should delete the Service Account or the workload identity provider associated with Anyscale's AWS account.
Edit custom resources
For Anyscale Clouds deployed with anyscale cloud register, you can modify the Filestore and Storage bucket ID. Prior to editing, Anyscale performs a static verification of cloud resources. If errors occur during this validation, review, and resolve any issues.
Filestore
Specify both the Filestore instance ID and location.
anyscale cloud edit CLOUD_NAME --gcp-filestore-instance-id=NEW_FILESTORE_INSTANCE_ID --gcp-filestore-location=LOCATION_OF_NEW_FILESTORE
Storage bucket ID
Use either of the following commands to modify the storage bucket ID.
anyscale cloud edit CLOUD_NAME --gcp-cloud-storage-bucket-name==NEW_STORAGE_BUCKET_ID
anyscale cloud edit --cloud-id=CLOUD_ID --gcp-cloud-storage-bucket-name==NEW_STORAGE_BUCKET_ID
To ensure that the edited Anyscale Cloud meets the requirements, add the optional flag --functional-verify workspace,service to anyscale cloud edit to launch a test workspace and service.
Editing and replacing resources doesn't automatically delete unused entities. You must separately delete any unwanted resources.
Control costs
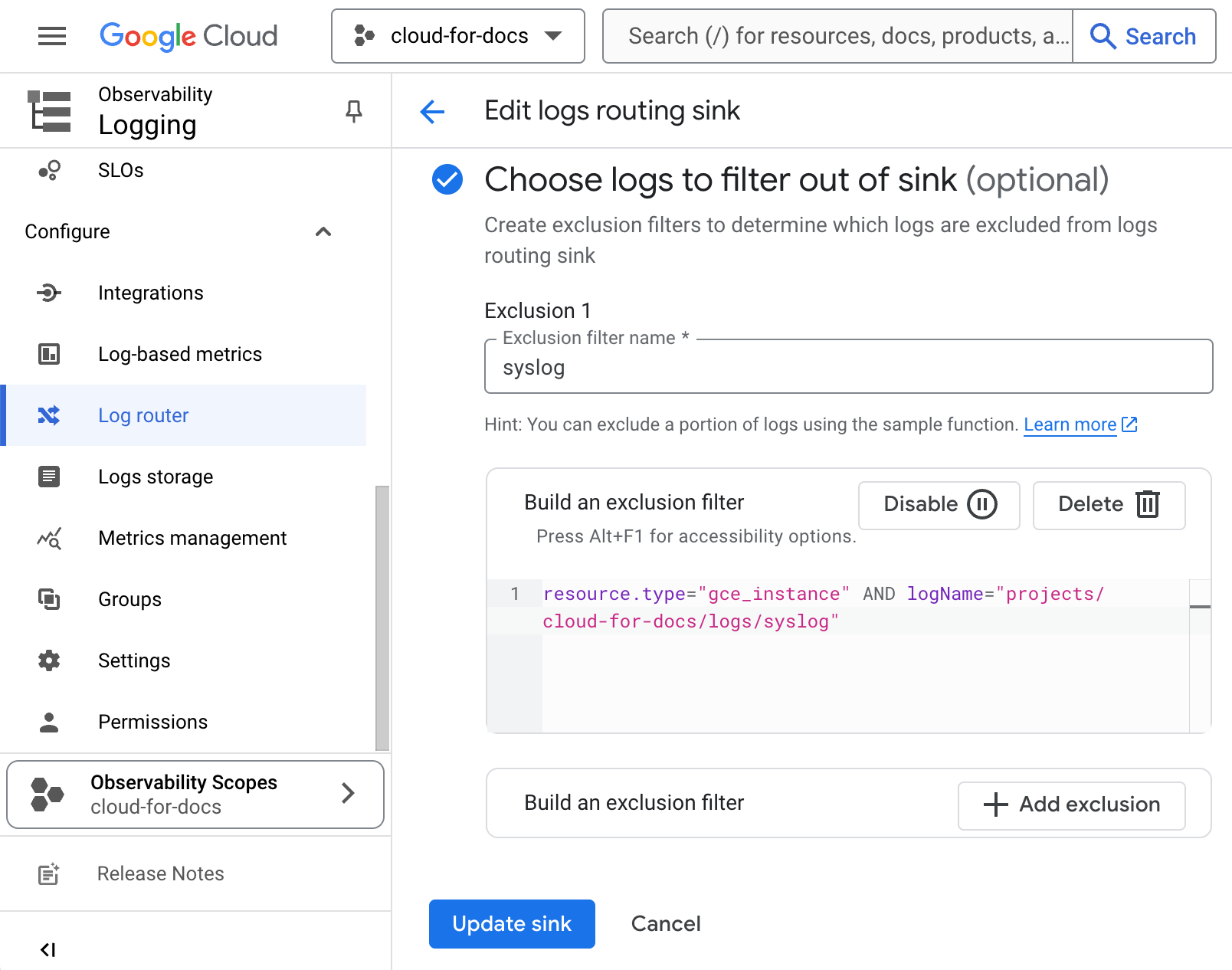
By default, GCP logs various activities, including those from Compute Engine instances (GCE), which may generate unexpected costs if not monitored. To filter out specific logs or exclude all logs related to GCE VMs, follow these steps:
-
Navigate to Log router.
-
For the
_Defaultsink, under More actions, select Edit sink. -
At the bottom, navigate to Choose logs to filter out of sink (optional), and type in the following, replacing
GCP_PROJECT_NAMEwith your project name:resource.type="gce_instance" AND logName="projects/GCP_PROJECT_NAME/logs/syslog"To exclude all GCE logs related to VMs, use the following:
resource.type="gce_instance"
Set a default Anyscale Cloud
Anyscale launches clusters in the default Cloud if you don't specify one. You can set a default Anyscale Cloud with this command:
anyscale cloud set-default ANYSCALE_CLOUD_NAME
Appendix: Minimal IAM Permissions for cloud edit
This section provides the minimal IAM permissions required for the Anyscale CLI to perform cloud edit. As an GCP administrator, follow these steps to apply the policy:
-
Create a new custom role or edit an existing role to include the following permissions.
- See GCP documentation on Create and manage custom roles for more information.
-
Grant the role to the service account that will be used to run the Anyscale CLI.
- See GCP documentation on Manage access to projects, folders, and organizations for more information.
compute.firewallPolicies.get
iam.serviceAccounts.getIamPolicy
iam.serviceAccounts.get
storage.buckets.getIamPolicy
compute.subnetworks.get
file.instances.get
compute.networks.get
resourcemanager.projects.getIamPolicy
resourcemanager.projects.get
redis.instances.get
storage.buckets.get
serviceusage.operations.get
serviceusage.services.enable
serviceusage.services.get