Access Amazon ECR
Access Amazon ECR
This section configures Amazon Elastic Container Registry access for Anyscale clusters. This setup is useful if you want to launch clusters with custom images stored in a private registry. This configuration consists of two steps:
- The IAM role used by Anyscale clusters needs the correct policies to read from ECR.
- The repository in ECR must grant access to the given IAM role.
Identify the IAM role used by Anyscale clusters
When deploying an Anyscale Cloud on AWS, Anyscale configures a default IAM role that is assumed by all Ray cluster nodes.
This IAM role follows this naming pattern if you set up the cloud using anyscale cloud setup:
<Anyscale Cloud ID>-cluster_node_role
For clouds created with anyscale cloud register, the role is specified through the flag --instance-iam-role-id.
You can also override the default IAM role by specifying an existing role in your compute configuration. See Specify an IAM role for an Anyscale cluster.
To determine the IAM role on a running cluster, execute:
aws sts get-caller-identity
Grant Permissions to the IAM role
Once you've identified the IAM role used by Anyscale clusters, you can grant the required permissions to that role.
Attach AmazonEC2ContainerRegistryReadOnly to the cluster node role
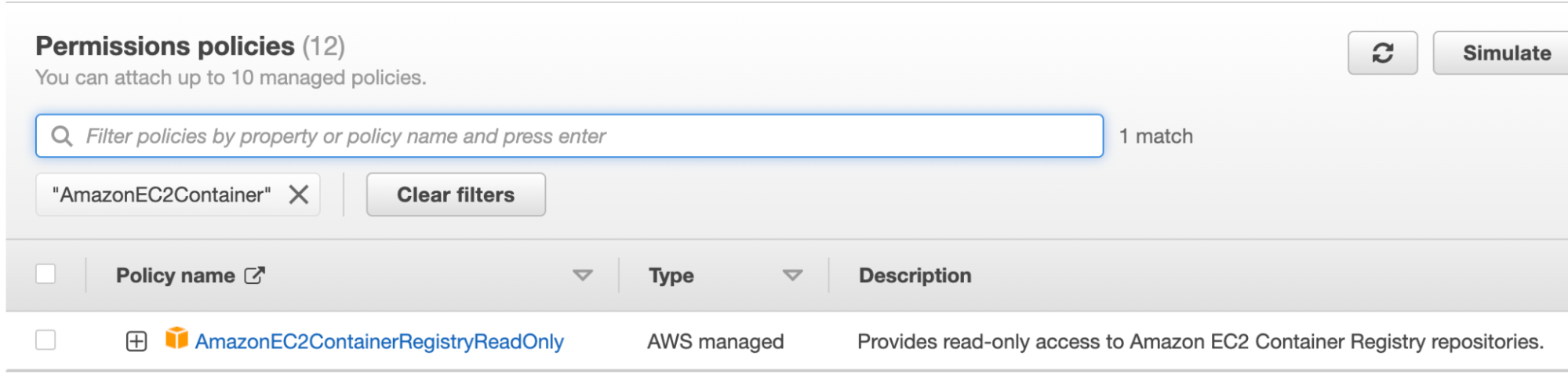
- Look in the Permissions policies section of your Role. If the role is assigned AmazonEC2ContainerRegistryReadOnly, no further action is required. If it does not, continue to set up the correct policies.
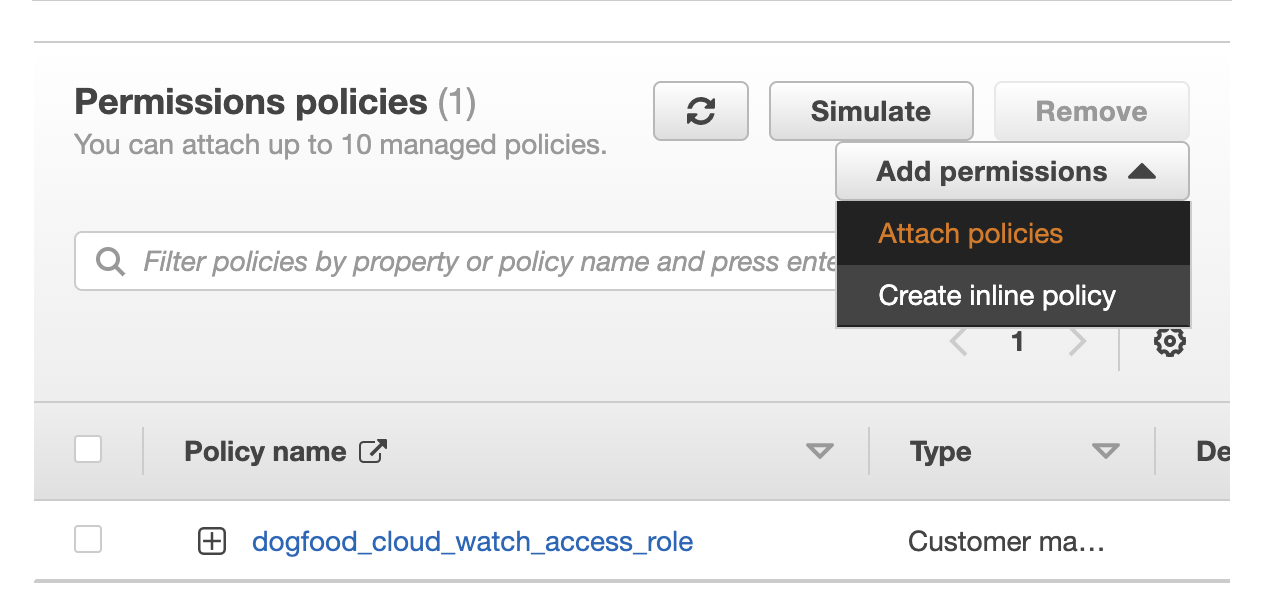
- Click Add Permissions and select Attach policies.
- Search for AmazonEC2ContainerRegistryReadOnly and select the policy.
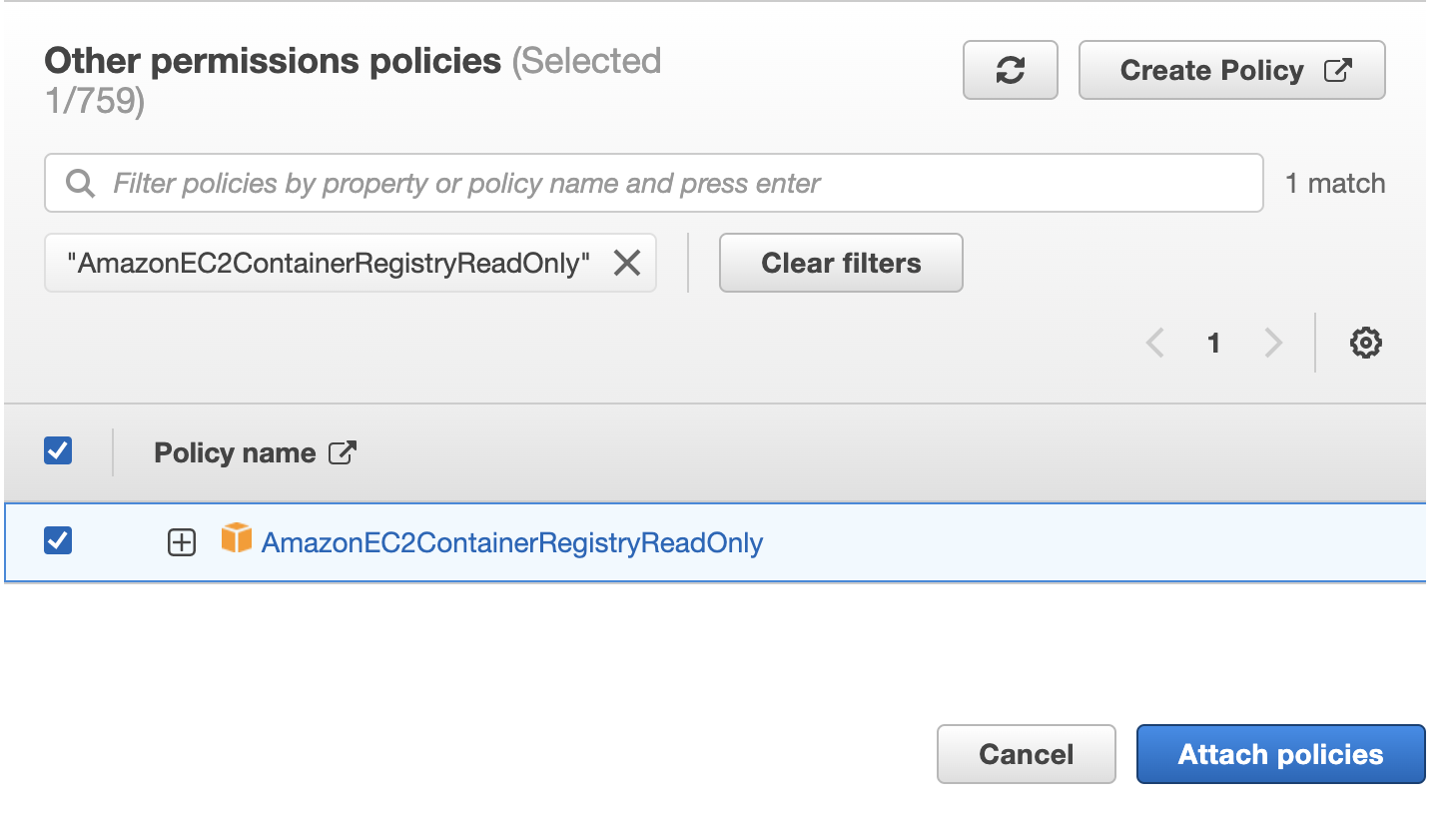
- Click Attach policies.
Grant the cluster node role access to a private ECR repository
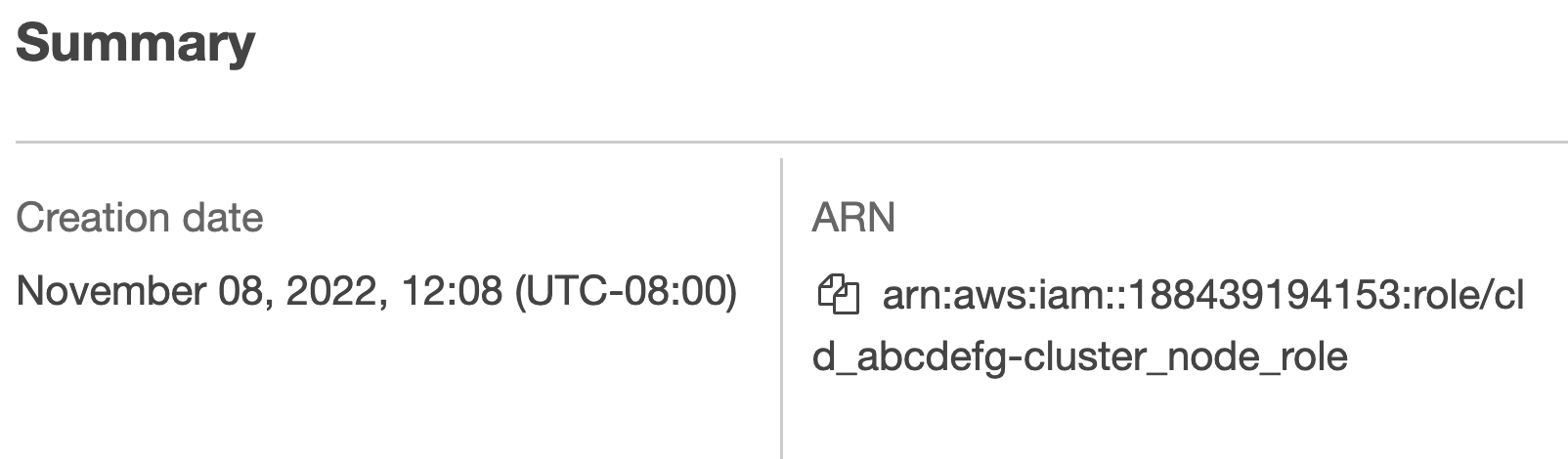
- Search for the Cluster Node Role on the AWS IAM page and select it.
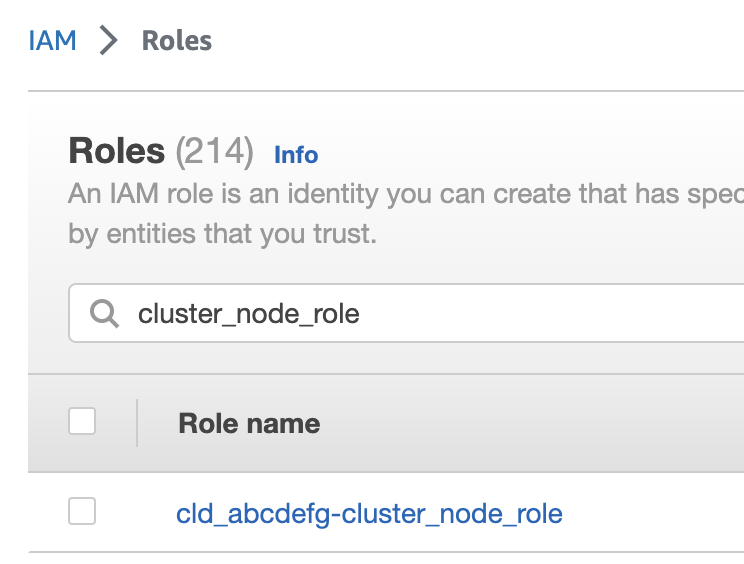
- Find and copy the ARN.
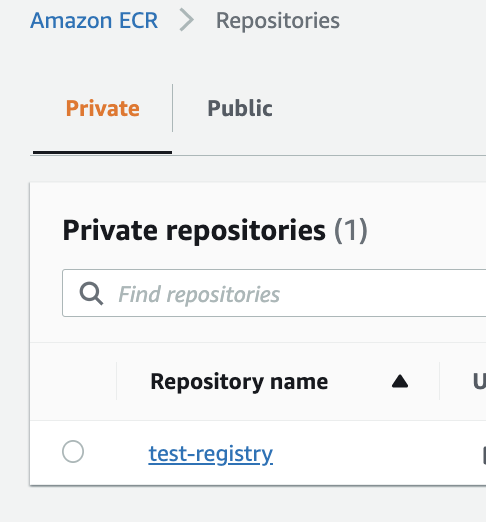
- Search for the private repo that you want to grant access to on the AWS ECR page and select it.
- Navigate to the Permissions section.
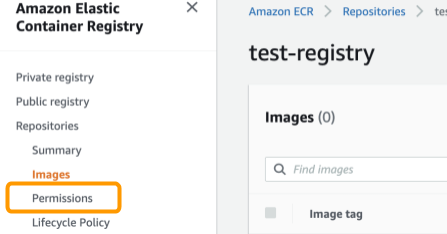
- Select Edit JSON Policy.

- Add the role ARN from step 2 into the
<REPLACE_WITH_ARN>field in the JSON below.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "AllowPull",
"Effect": "Allow",
"Principal": {
"AWS": "<REPLACE_WITH_ARN>"
},
"Action": [
"ecr:BatchCheckLayerAvailability",
"ecr:BatchGetImage",
"ecr:DescribeImageScanFindings",
"ecr:DescribeImages",
"ecr:DescribeRepositories",
"ecr:GetAuthorizationToken",
"ecr:GetDownloadUrlForLayer",
"ecr:GetLifecyclePolicy",
"ecr:GetLifecyclePolicyPreview",
"ecr:GetRepositoryPolicy",
"ecr:ListImages",
"ecr:ListTagsForResource"
]
}
]
}
Once this step is completed, nodes launched by Anyscale should have access to your private registry.